Security
Common patterns and trends from cyber-attack data
Lessons learned from past cyber assaults can help companies protect themselves from data breach in the future. Mohamed Dabo looks at a NuData report that identifies recurrent features of cyber attacks from the trove of data collected by Mastercard.

T
he Covid-19 pandemic has driven the fastest transition of customers moving to online transactions. As a result, we’ve seen an unprecedented surge in the creativity of credential-stealing scams.
Companies adapting their business models to enhance online servicing have to grapple with growing customer needs and more sophisticated attacks.
From January 1 to June 30, NuData analysts closely monitored global online changes and summarised the key findings to help make sense of what’s changing in the threat landscape.
This article highlights five cybersecurity facts from the latest NuData report: 2020 H1 Fraud risk at a glance.
1. More attacks look like humans
About 96% of attacks on financial institutions were sophisticated – those that make extra effort to emulate human behaviour.
Bad actors continue their shift to more complex schemes, attempting to fool security tools that can only detect basic bot behaviour. Financial institutions (FIs) receive the highest percentage of sophisticated attacks amongst all industries, with 96% in the first half of 2020, up from 90% in 2019.
The researchers expect to continue seeing human-looking attacks increase across all industries.
As companies get wise to fraudsters and improve their bot-detection tools, fraudsters are forced to find another way in. Many are relying on more sophisticated attacks to help them access protected platforms.
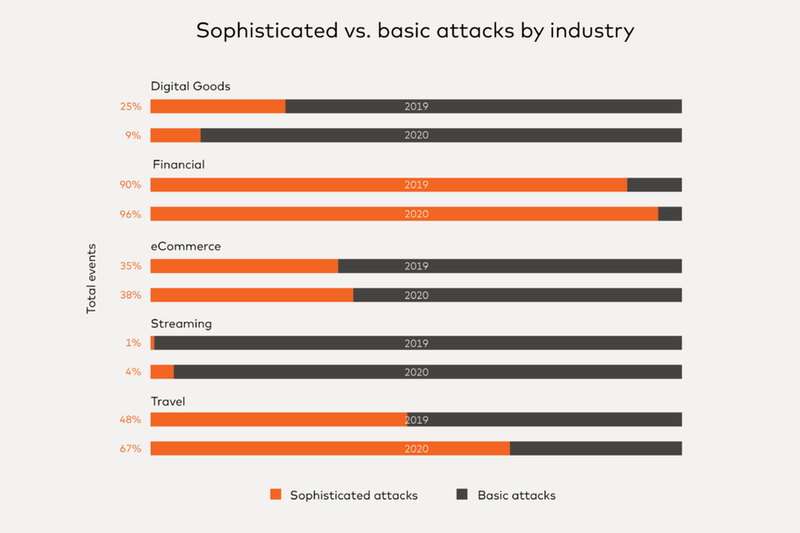
Sophisticated vs basic attacks by industry. Credit: NuData
Account creation attacks increased during the Covid-19 lockdowns
High-risk account creation attempts against a number of merchants increased drastically in the first half of 2020 after the lockdowns began.
In this type of attack, fraudsters create new accounts to buy goods with stolen card information or buy sought-after and restricted goods at a mass scale for later resale. In particular, from March to June, one in every two account creation attempts was flagged as high risk by the NuData platform.
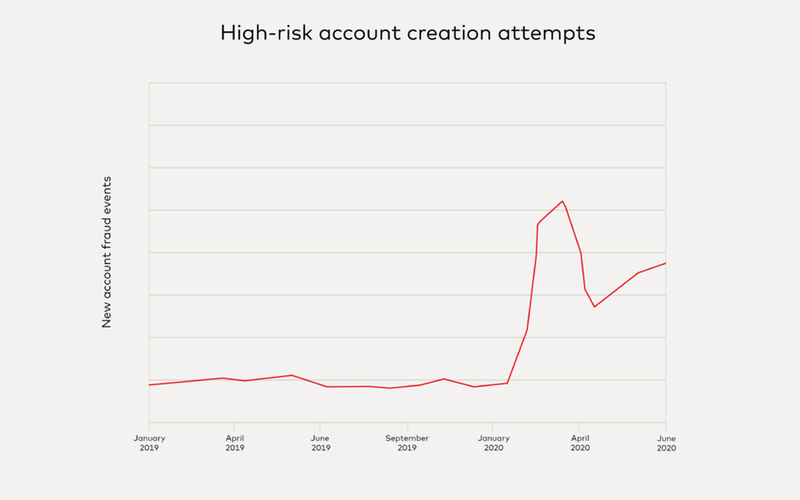
High-risk account creation attempts. Credit: NuData
3. Chargeback dollar values more than doubled
In situations of crisis, chargebacks tend to increase across retail companies.
Once the lockdowns began in North America, the average dollar value of a chargeback grew by 124% for in-store pickups, compared to the average value before the movement restrictions.
Chargebacks from in-store pickups also grew in volume: more than 100% in April.

Daily chargeback amount by delivery type. Credit: NuData
4. More attacks go mobile
While attacks on desktop continue at higher levels, attacks from mobile devices have been growing.
High-risk traffic grew by 55% from January to June 2020.
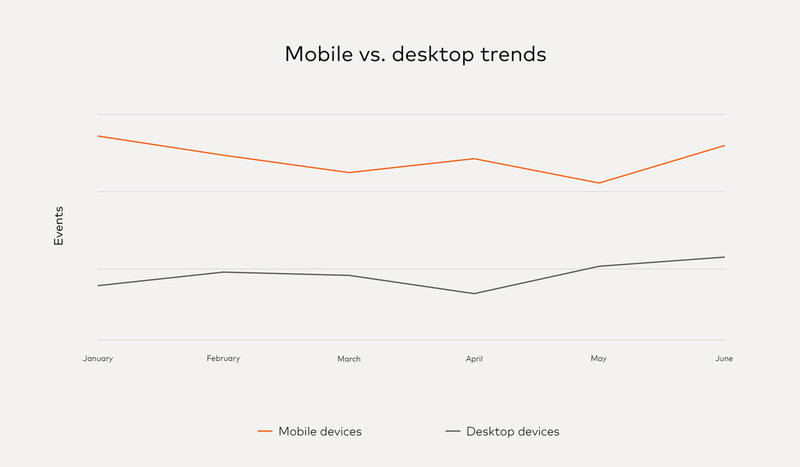
Mobile vs. desktop trends. Credit: NuData
5. Account takeover is the most common attack across industries
Looking at attack types by industry tells us which are at higher risk. Account takeover attacks (ATOs) at login make up most of the attack traffic.
This is unsurprising considering these attacks are deployed at a larger scale than others as login credentials are easier and cheaper to access than other types of user information.
Travel and retail received a wider variety of attacks, with travel showing an even distribution between login and checkout attacks.
During the lockdowns, these two industries experienced the biggest fluctuation, with travel attacks at checkout climbing to 58% of total high-risk events in February.
Risky activity in retail account validation pages (pages where customers can access information such as booking info, number of reward points, order status, or account profile) reached 65% in March.

Attack types by industry. Credit: NuData
6. What the data shows about fraud in 2020
With the world experiencing an overwhelming pandemic, businesses identified ways to increase their online goods and service delivery.
Opportunistic fraudsters responded quickly as well. As we’ve seen, high-risk traffic at account-creation grew in the first half of 2020, primarily after lockdowns began.
Meanwhile, attackers increased their use of sophisticated techniques to increase the chances of high-value attacks, especially when targeting financial institutions.
The inclusion of behavioural tools in the security strategy is helping companies detect fraud at every level, including human-looking attacks, to prevent these online threats.
The good news is that by analysing individual attack vectors, companies leveraging NuData tools can find common patterns to help prevent future attacks.
Many of them use IP addresses or devices linked to past malicious behaviour – in this case, detected because the NuData Trust Consortium leveraged the historical intelligence on those data points.
This highlights the value of machine learning and a Consortium to recognise previously seen patterns in new attacks, as well as risky parameters.

Cybercrime concept. Credit: NuData
7. Reporting the cyber attack
From a law enforcement perspective, one of the most important things when it comes to cyber attacks is to report the incident to the police, said Jim Stokley, deputy director of the National Crime Agency’s National Cyber Crime Unit (NCCU):
“Organisations can rest assured that by reporting incidents to the police, no information will be shared with regulators. You are a victim of a crime, and the information we have will be treated as confidential.
“But reporting the incident is important because it enables us to adapt and respond to the threat as well as being able to investigate it, and any resultant prosecution can act as a deterrent for cyber criminals in future.
“So I encourage all organisations that are hit by cyber attacks to report those incidents to the police.”